GitHub embraces Swift and provides code analysis, security alerts and dependency updates for Swift projects
GitHub released significant updates for Swift developers this summer.
Swift is now supported for the following GitHub tools:
CodeQL: semantic code analysis to detect security vulnerabilities
Dependabot: security alerts and dependency updates
CodeQL and Swift
Tim Condon wrote an excellent guide on how to set up CodeQL for a Swift project.
An interesting key takeaway is you cannot use github/codeql-action/autobuild@v2 in your GitHub action workflow to build Swift packages. You have to replace that step with an explicit swift build .
Dependabot and Swift
Setup was a breeze and straightforward thanks to a guided process for creating the necessary dependabot.yml configuration file.
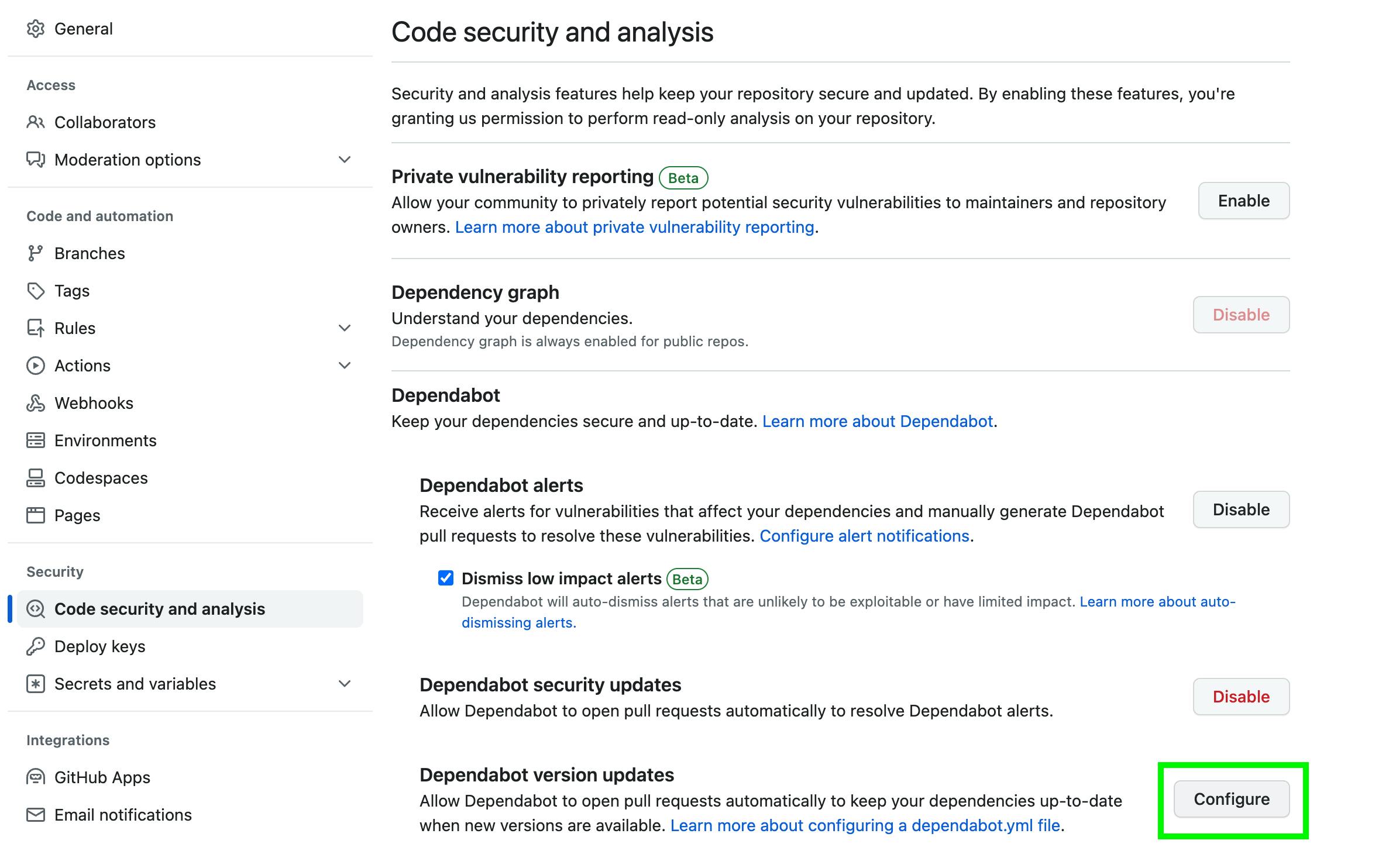
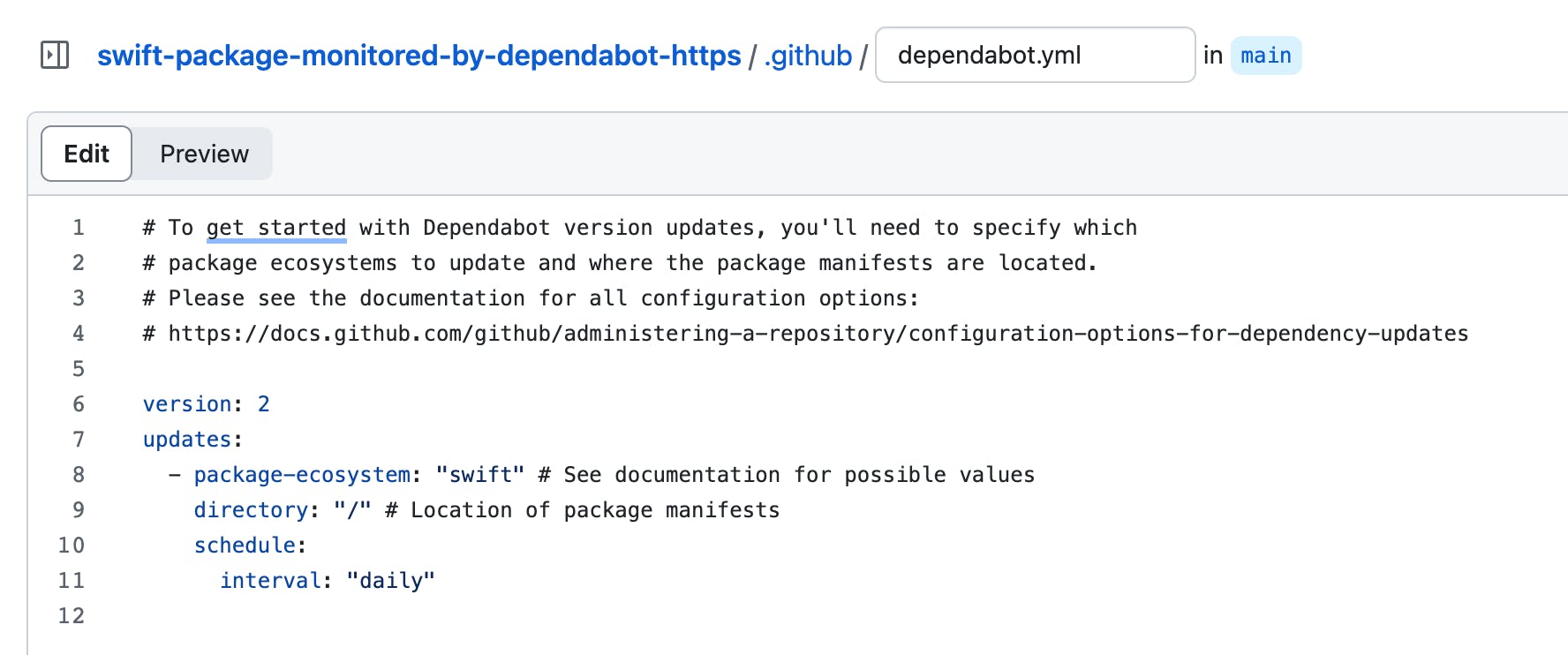
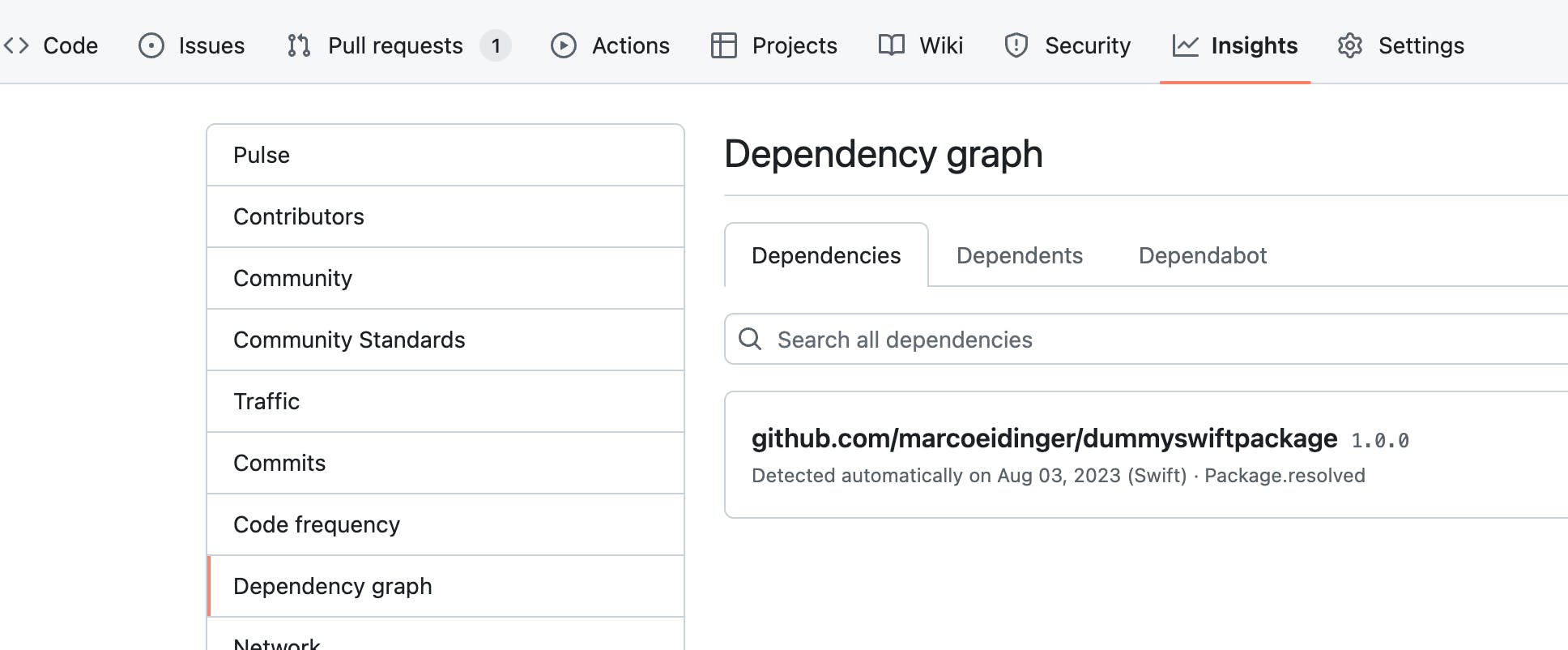
Nice to see my package dependencies in Github's Dependency graph view.
Dependabot will check for version updates according to the interval maintained in the yml file or I can trigger a manual check.
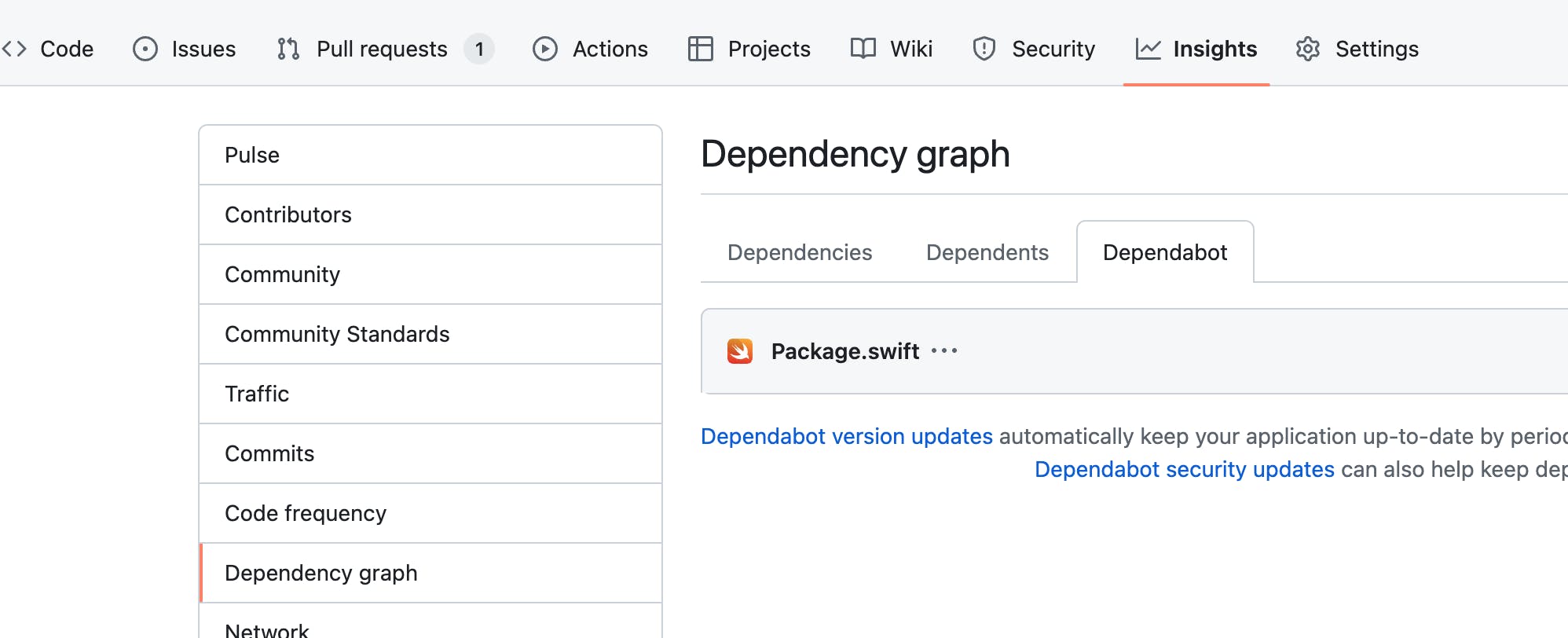

I stumbled over two issues.
First, there is a bug when using scp-style URIs. This bug should be fixed soon but you can avoid it by using https links in your Package.swift and Package.resolved files
// GOOD
dependencies: [.package(url: "https://github.com/MarcoEidinger/DummySwiftPackage.git", .upToNextMajor(from: "1.0.0"))
// BAD
dependencies: [.package(url: "git@github.com:MarcoEidinger/DummySwiftPackage.git", .upToNextMajor(from: "1.0.0"))
You can track the status of the bug fix in the following GitHub issue I created.
Second, the Depandabot logic to update dependencies is different from the behavior using Swift Package Manager (SPM).
swift package update will honor the version requirement .upToNextMajor(from: "1.0.0") by only updating Package.resolved for patch and minor releases.
Dependabot may create a PR to update Package.swift and Package.resolved for you to change the version requirement.
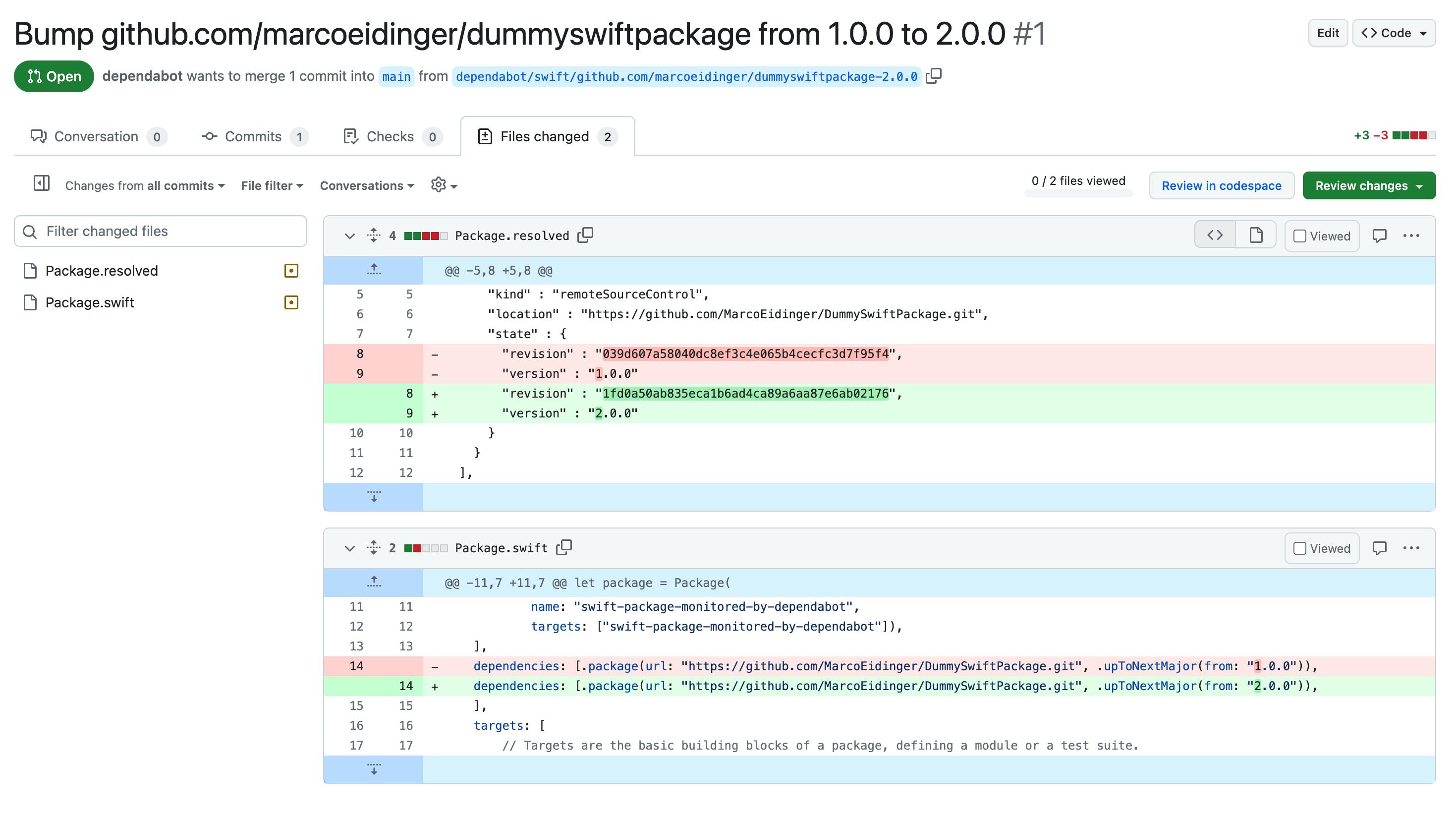
I like the Depandabot logic offering to bump up the major version but it was unexpected.
David Rodríguez told me that GitHub will support versioning-strategies soon so that developers can choose their preferred update strategy.
Conclusion
Such tool support is fantastic for Swift developers, especially for server-side development as the GitHub Advisory Database warns about several vulnerabilities in Swift when using Vapor, swift-nio-http2 or grpc-swift.
I am also excited to see built-in support for dependency update management.
Probably this was inspired by community projects for GitHub actions like swift-package-dependencies-check or action-xcodeproj-spm-update.
name: Package Update
on:
workflow_dispatch:
schedule:
- cron: '0 6 * * 1' # Monday at 06:00 UTC
jobs:
dependencies:
uses: MarcoEidinger/swift-package-dependencies-check/.github/workflows/reusableWorkflow.yml@v2
with:
commit-message: 'Package update'
Above you see an example on how SwiftPackageIndex-Server updates their packages and I am curious if Dave or Sven plan to migrate to Dependabot.

